Configure Unifi to block access from one (IoT) VLAN to all VLANs
After setting up a Pi-hole DNS server for my IoT network VLAN, it was time to configure the internal firewall so that devices on it wouldn’t be able to communicate with the other VLANs in an unsolicited way. Ubiquiti has an article posted on their site which lays the foundation for this goal, but it doesn’t quite meet my requirements because I need all the other VLANs to be able to communicate with each other, and the IoT VLAN, while also allowing traffic from the IoT VLAN to pass back to the initiating device.
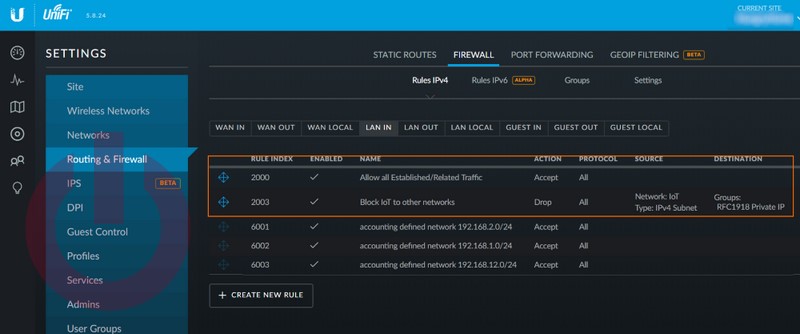
Two rules are required to accomplish this, and the order is important so lets start with the first one by navigating to the LAN IN table of the Firewall section in settings.
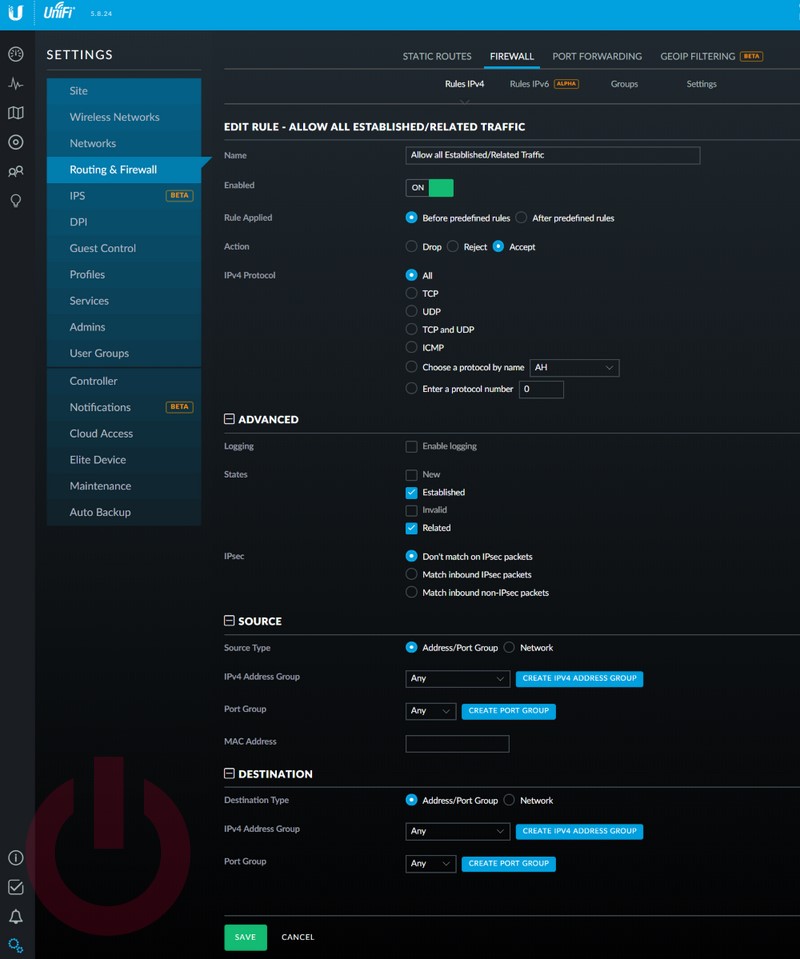
- Allow rule: This rule will enable the talk back traffic from IoT to the other unrestricted VLANs.
- The name isn’t important, but it is useful to have something descriptive, so call it “Allow all Established/Related Traffic”.
- Set the Action to “Accept”
- Check “Established” and “Related” in the States section.
- Set the Source and Destination to “Any/Any”
- Deny rule: This rule will block all traffic (that isn’t established/related) from the IoT VLAN to the others.
- Set name to “Block IoT to other networks”
- Set Action to “Drop”
- In the SOURCE section, change “Address/Port Group” to “Network” and select the IoT VLAN network.
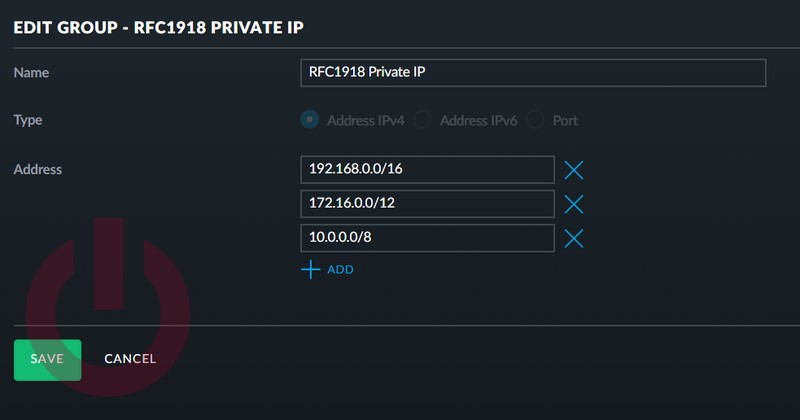
- In the DESTINATION section, click “CREATE IPv4 ADDRESS GROUP” and define a group which includes all the private IPv4 IP addresses (192.0.0.0/16, 172.16.0.0/12, 10.0.0.0/8) defined in RFC1918.
Then select this group as the “IPv4 Address Group”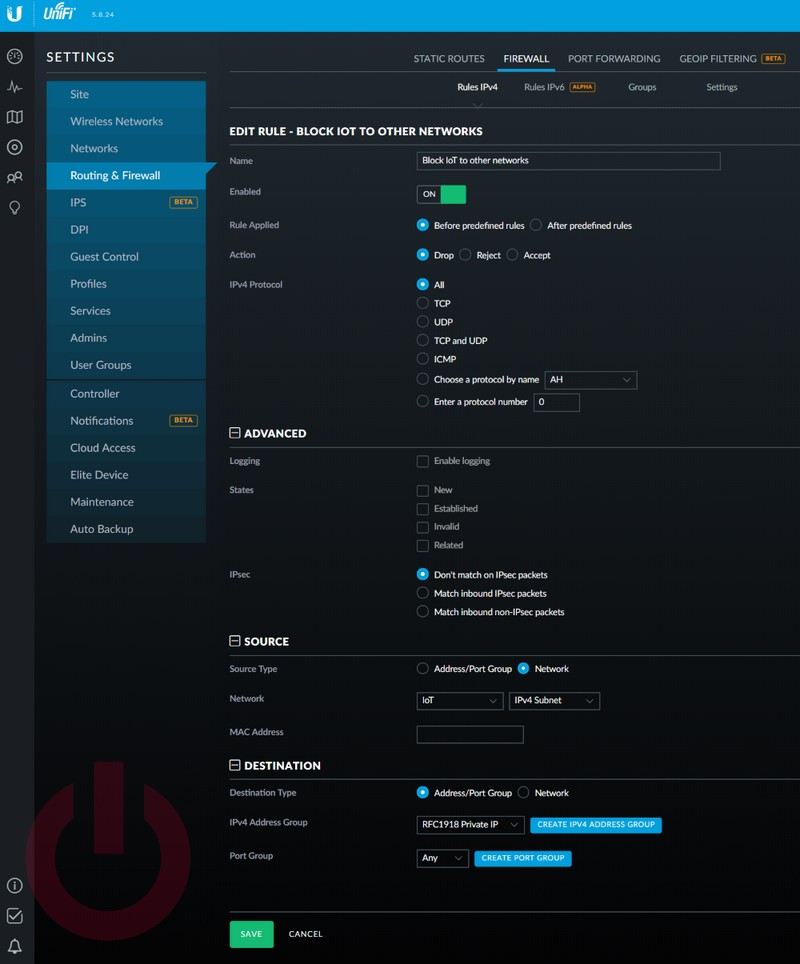
The ordering of these rules is essential. It will not work correctly if they are the other way around. They should get sorted in the order they are created, but if for some reason they don’t. You can reorder them using the Chrome browser by grabbing the four directional icon on the left side and ordering the way you want. AFAIK, this only works in Chrome.
